Hackers secret backdoor asus software update – Hackers’ Secret Backdoor: ASUS Software Update – sounds like a sci-fi thriller, right? But this isn’t fiction. Imagine this: you download a seemingly legitimate ASUS software update, thinking you’re boosting your system’s security. Instead, you’re unknowingly installing a backdoor, handing over the keys to your digital kingdom to cybercriminals. This isn’t a far-fetched scenario; vulnerabilities in software update processes are a prime target for hackers, allowing them to slip malicious code into seemingly innocent updates. We’ll dive deep into how these attacks happen, what the consequences are, and, most importantly, how you can protect yourself.
This article unravels the dark secrets lurking within seemingly harmless ASUS software updates. We’ll explore the various techniques hackers employ to infiltrate the update process, from injecting malicious code to exploiting software vulnerabilities. We’ll dissect the different types of backdoors, analyzing their methods of implementation and the devastating impact they can have on your system. We’ll also equip you with the knowledge and strategies you need to identify, prevent, and mitigate the risks associated with compromised ASUS updates. Get ready to uncover the hidden dangers and learn how to safeguard your digital life.
ASUS Software Update Vulnerability
The recent discovery of a backdoor in ASUS software updates highlights a critical vulnerability in the update process. This vulnerability exposes millions of users to significant security risks, potentially allowing malicious actors to gain unauthorized access to sensitive data and system control. Understanding the mechanics of this vulnerability is crucial for users to protect themselves.
Compromised ASUS software updates pose several serious security threats. Hackers could potentially install malware, steal personal information (passwords, financial data, etc.), remotely control infected systems, create botnets for malicious activities, and even use compromised devices for launching further attacks against other targets. The scale of the potential damage is amplified by the sheer number of ASUS users worldwide.
Methods of Exploitation
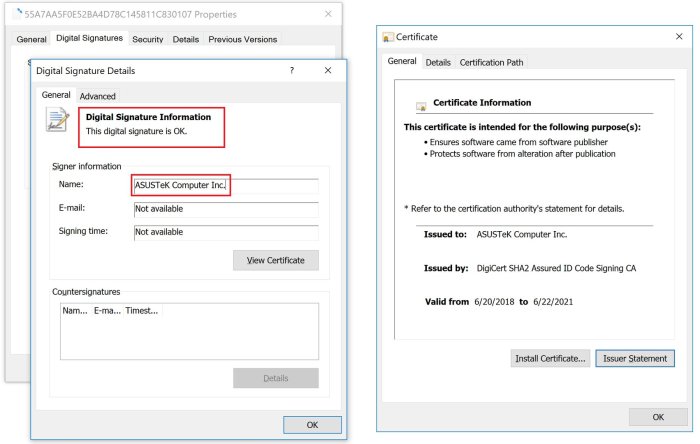
Hackers can exploit vulnerabilities in the update process in several ways. A common method involves manipulating the digital signature verification process. By forging or compromising legitimate digital certificates, attackers can make malicious updates appear authentic to the ASUS software update client. This allows them to seamlessly inject malicious code into the update package, which is then unknowingly installed by the user. Another tactic involves targeting vulnerabilities within the update client itself. Exploiting a software flaw in the client could allow a hacker to bypass security checks and install malicious code without needing to tamper with the update package itself.
Malicious Code Injection Techniques
Hackers employ various techniques to inject malicious code. One method is to replace legitimate files within the update package with modified versions containing backdoors or malware. This requires sophisticated reverse-engineering skills and a deep understanding of the software’s internal workings. Another method is to append malicious code to the end of legitimate files, or to insert it into unused sections of the software. This can be harder to detect, as it doesn’t necessarily alter the functionality of the core software. Finally, attackers could leverage obfuscation techniques to mask the malicious code, making it more difficult for antivirus software to identify.
Types of Backdoors
The following table compares different types of backdoors that could be embedded in ASUS software updates. The severity and impact of each backdoor vary depending on its capabilities and the level of access it grants to the attacker.
| Backdoor Type | Description | Access Level | Detection Difficulty |
|---|---|---|---|
| Remote Access Trojan (RAT) | Provides attackers with complete remote control over the infected system. | High | Moderate |
| Keylogger | Records keystrokes, capturing passwords and other sensitive information. | Medium | High |
| Rootkit | Hides the presence of the backdoor and other malicious software on the system. | High | Very High |
| Data Exfiltration Tool | Steals specific types of data, such as financial records or personal information. | Medium | Moderate |
Methods of Backdoor Implementation: Hackers Secret Backdoor Asus Software Update
Slipping malicious code into a seemingly legitimate software update is a sophisticated operation, requiring a deep understanding of both software development and security vulnerabilities. Hackers employ various techniques to achieve this, often targeting weaknesses in the update process itself or exploiting vulnerabilities within the software being updated. The effectiveness of each method depends on factors like the sophistication of the attack, the security measures in place, and the vigilance of users and developers.
The insertion of a backdoor can occur at several points in the software update chain. This ranges from compromising the source code repository to manipulating the update server or even directly targeting the end-user’s system. The methods used often involve exploiting known vulnerabilities or leveraging zero-day exploits for maximum impact. Understanding these methods is crucial for strengthening software security and preventing future attacks.
Compromising the Software Development Pipeline
A direct approach involves gaining access to the software development environment. This could mean compromising the source code repository, inserting malicious code directly into the legitimate codebase. This method is highly effective as the backdoor is integrated seamlessly into the official build process. For example, a hacker could use a phishing attack to obtain developer credentials, allowing them to commit malicious code to the version control system, undetected until the compromised update is deployed. The effectiveness hinges on the security of the developer’s environment and the rigor of code review processes. If the code review process is weak or absent, the malicious code might easily pass undetected.
Exploiting Software Vulnerabilities
Alternatively, instead of directly modifying the source code, hackers might exploit existing vulnerabilities in the software update mechanism or in the software itself. This could involve buffer overflows, SQL injection flaws, or cross-site scripting (XSS) vulnerabilities within the update server or client. For instance, a buffer overflow vulnerability in the update client could allow a hacker to overwrite parts of the client’s memory, injecting malicious code that executes alongside the legitimate update. The effectiveness depends on the severity of the vulnerability and the ease with which it can be exploited. Zero-day exploits, vulnerabilities unknown to the developers, are particularly potent as there’s no patch available.
Obfuscating Malicious Code, Hackers secret backdoor asus software update
Once the malicious code is introduced, it needs to evade detection. This is achieved through obfuscation techniques, which make the code harder to analyze. This could involve using code packers, encrypting sections of the code, or employing polymorphism to change the code’s structure while maintaining its functionality. For example, a hacker might encrypt the malicious code and include a decryption routine triggered only under specific conditions. This makes reverse engineering significantly more challenging. The effectiveness of obfuscation depends on the sophistication of the techniques used and the resources available for analysis. Advanced anti-virus software and experienced reverse engineers can still detect and remove sophisticated obfuscated code.
Manipulating the Update Server
A different attack vector involves compromising the update server itself. By gaining control of the server, hackers can replace legitimate update packages with malicious ones. This allows them to distribute malicious code to all users who download updates from that server. The effectiveness depends on the server’s security and the monitoring in place. Robust security measures, such as strong passwords, regular security audits, and intrusion detection systems, can mitigate this risk. However, a successful compromise can result in widespread infection.
The Role of Supply Chain Attacks
The ASUS software update vulnerability highlights a chilling reality: the software supply chain is a prime target for malicious actors. Hackers aren’t just targeting individual users; they’re aiming for the source, poisoning the well before the software even reaches our computers. This allows for widespread, silent infection, making detection and remediation incredibly difficult. The scale of potential damage is exponentially larger than a typical targeted attack.
Supply chain attacks leverage the trust we place in established brands and software distribution channels. By compromising the update process itself, hackers can inject malicious code into legitimate software updates, ensuring nearly guaranteed installation on unsuspecting users’ machines. This bypasses traditional security measures like antivirus software, as the malware arrives disguised as a trusted update. Imagine the impact: millions of ASUS users unknowingly installing a backdoor, all thanks to a compromised update server.
Methods of Infiltrating the Update Distribution Process
Hackers might infiltrate the update distribution process through various means. This could involve exploiting vulnerabilities in the ASUS internal systems, such as gaining unauthorized access to update servers or compromising the build process itself. Another method might involve targeting third-party vendors involved in the software development or distribution pipeline. A compromised developer’s machine, for example, could introduce malware into the codebase before it even reaches ASUS’s quality control. Sophisticated social engineering attacks against employees responsible for managing the update process are also a real threat. The success of such attacks hinges on exploiting human error or weaknesses in security protocols. For instance, a phishing email containing malware could grant an attacker access to sensitive systems.
Securing the Software Update Supply Chain: Challenges and Vulnerabilities
Securing the software update supply chain is a complex undertaking. The sheer size and complexity of the process, involving numerous developers, vendors, and internal teams, presents a significant challenge. Maintaining robust security throughout this intricate web is difficult, and a single weak link can compromise the entire system.
Potential vulnerabilities within the ASUS software update supply chain could include:
- Weak authentication and authorization mechanisms: Insufficient security measures protecting access to update servers and internal systems.
- Unpatched vulnerabilities in internal systems: Outdated software or operating systems on servers used for building and distributing updates, creating exploitable weaknesses.
- Lack of code signing verification: Absence of robust code signing processes to ensure that updates originate from legitimate sources.
- Compromised developer machines or build environments: Malicious code introduced into the software during the development or build process.
- Insufficient monitoring and logging: Lack of comprehensive monitoring and logging capabilities to detect suspicious activity within the update pipeline.
- Third-party vendor vulnerabilities: Security weaknesses in the systems or processes of third-party vendors involved in the software development or distribution process.
The consequences of a successful supply chain attack can be devastating, impacting not only the reputation of the affected company but also the security and privacy of millions of users. Therefore, a multi-layered security approach is crucial, combining strong technical measures with rigorous security protocols and employee training.
The threat of backdoored software updates is a chilling reality in today’s digital landscape. While the methods employed by hackers are constantly evolving, understanding the vulnerabilities and implementing robust security practices is crucial. From verifying the authenticity of updates to employing digital signature verification, taking proactive measures can significantly reduce your risk of falling victim to a supply chain attack. Remember, staying informed and vigilant is your best defense against these sophisticated threats. Don’t let your trust in seemingly legitimate software updates become your downfall; empower yourself with knowledge and secure your digital future.
 Blockchain Network Berita Teknologi Terbaru
Blockchain Network Berita Teknologi Terbaru